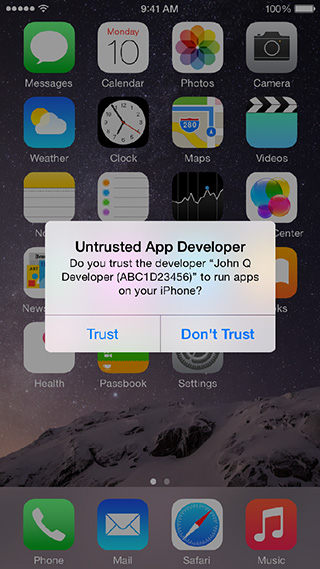
Earlier in the week, cybersecurity firm FireEye revealed a vulnerability in iOS called “Masque Attack,” which allows third-party, malicious applications to replace legitimate apps on an iOS device, that can then collect important, secure information right from the device.
Apple has now issued a statement to iMore on the issue:
“We designed OS X and iOS with built-in security safeguards to help protect customers and warn them before installing potentially malicious software,” an Apple spokesperson told iMore. “We’re not aware of any customers that have actually been affected by this attack. We encourage customers to only download from trusted sources like the App Store and to pay attention to any warnings as they download apps. Enterprise users installing custom apps should install apps from their company’s secure website.”
Masque Attack can use a replaced application to do several different things, namely retrieve information from the user as they insert important information, including email addresses, phone numbers, passwords and more. What’s more, the researches also found that after a genuine application is replaced, the information stored within the original app’s cache is still there, and accessible through the malware-infested app.
Recently, another major compromise to iOS and the platform’s apps was found to be targeting Chinese iPhone/iPad users, with an attack known as “WireLurker,” which could also infiltrate iOS-based devices through a USB connection. Soon after, Apple issued a similar statement reminding users not to download untrusted applications, and to only download apps from a trusted source, like the App Store.


Recent Comments